Tag: CHAP
Configuring CCNA&RS VTP HSTP GRE IPsec EIGRP Done Cisco Packet Tracer
Configuring CCNA&RS VTP HSTP GRE IPsec EIGRP Done Cisco Packet Tracer 7.0
This lab simulate a cisco LAN/WAN technologies that is part of the Cisco CCNA exam version 3.0

a) Configure and verify PPP. Find out on routers R2 and R3
b) Configure and verify single-homed branch connectivity using eBGP IPv4.
c) Configure EIGRP for IPv4
d) Mutual redistribute EIGRP and BGP
e) Configure and verify GRE tunnel connectivity and IPsec
Configure and verify PPP. Find out on routers R2 and R3
[wpanchor id=”configure_and_verifyppp”]
On R2 and R3
a.1) PPP configured on R2. R2 is the DCE interface you can configured a clock rate.
interface Serial0/3/1
ip address 170.16.6.2 255.255.255.252
encapsulation ppp
ppp authentication chap pap
clock rate 2000000
username R2 password 0 cisco
a.2) PPP configured on R3.
interface Serial0/3/1
ip address 170.16.6.1 255.255.255.252
encapsulation ppp
ppp authentication chap
username R3 password 0 cisco
You must to create a username R2 on the router R3 and vice-versa.
b) Configure and verify single-homed branch connectivity using eBGP IPv4(< a href="backmenu">menu)
The router R2 is connected to the router R3
b.1) Configure BGP on R2
R2#show run | b router
<... omitid ...>
router bgp 65535
bgp log-neighbor-changes
no synchronization
neighbor 170.16.6.1 remote-as 64000
network 170.16.6.0 mask 255.255.255.252
network 20.20.20.20 mask 255.255.255.255
redistribute eigrp 44
redistribute static
redistribute connected
<... omitid ...>
b.2) Configuration of BGP on R3
The BGP on R3 has 2 neighbors R5(AS 65534) and R2(AS 65535).
R3#show run | b router
<... omitid ...>
router bgp 64000
bgp log-neighbor-changes
no synchronization
neighbor 170.16.6.2 remote-as 65535
neighbor 170.16.4.2 remote-as 65534
network 170.16.5.0 mask 255.255.255.0
network 170.16.4.0 mask 255.255.255.0
network 170.16.6.0 mask 255.255.255.0
<... omitid ...>
b.3) Configuration of BGP on Router R5
router bgp 65534
bgp log-neighbor-changes
no synchronization
neighbor 170.16.4.1 remote-as 64000
network 170.16.4.0 mask 255.255.255.0
c)Configure EIGRP for IPv4(Menu)
EIGRP is configured on all the routers R1, R2, R4 and R5. The routers R2 and R5 are edge routers, where BGP is configured.
c.1) EIGRP on router R1
R1#show run | b router
router eigrp 44
eigrp router-id 1.1.1.1
network 172.16.2.0 0.0.0.255
network 192.168.16.0
network 30.0.0.0
c.2) EIGRP on router R2
router eigrp 44
eigrp router-id 2.2.2.2
redistribute bgp 65535 metric 1000000 10 255 255 1500
redistribute static
network 172.16.2.0 0.0.0.255
network 10.0.0.0
c.3) EIGRP on router R4
R4#show run | b router
router eigrp 44
eigrp router-id 4.4.4.4
network 172.16.1.0 0.0.0.255
network 192.168.17.0 0.0.0.255
network 192.168.16.0 0.0.0.255
no auto-summary
c.4) EIGRP on router R5
R5#show run | b router
router eigrp 44
eigrp router-id 5.5.5.5
network 172.16.1.0 0.0.0.255
no auto-summary
d)Mutual redistribute EIGRP and BGP(Menu)
The mutual redistribute between EIGRP and BGP is configure on R2 and R3
R2#show run | b router
router eigrp 44
eigrp router-id 2.2.2.2
redistribute bgp 65535 metric 1000000 10 255 255 1500
redistribute static
network 172.16.2.0 0.0.0.255
network 10.0.0.0
!
router bgp 65535
bgp log-neighbor-changes
no synchronization
neighbor 170.16.6.1 remote-as 64000
network 170.16.6.0 mask 255.255.255.252
network 20.20.20.20 mask 255.255.255.255
redistribute eigrp 44
redistribute static
redistribute connected
<... omitid ...>
e) Configure and verify GRE tunnel connectivity and IPsec(menu)
Configuring the GRE tunnel between the router R1 and R3
e.1) Configure the tunnel on R1
R1#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#interface tunnel 0
R1(config-if)#ip address 10.10.10.1 255.255.255.0
R1(config-if)#mtu 1476
R1(config-if)#tunnel source GigabitEthernet0/1
R1(config-if)#tunnel destination 170.16.6.1
e.1.1)Verify the interface tunnel
R1#show ip interface tunnel 0
Tunnel0 is up, line protocol is up
Internet address is 10.10.10.1/24
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1476 bytes
e.2) Configure tunnel on R3
R3#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#interface tunnel 0
R3(config-if)#ip address 10.10.10.2 255.255.255.0
R3(config-if)#mtu 1476
R3(config-if)#tunnel source Serial0/3/1
R3(config-if)#tunnel destination 172.16.2.2
Verifying the interface tunnel on R3
R3#show ip interface tunnel 0
Tunnel0 is up, line protocol is up
Internet address is 10.10.10.2/24
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 1476 bytes
<... omitid..>
The GRE is activated R1 and R3 the show ip interface is saying in both interfaces that tunnel0 is up and line protocol is up.
The ping from R1 to R3(10.10.10.2) should be Successful as you can see on the paragraph:
R1#ping 10.10.10.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.10.10.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/3 ms
e.2 Verifying and enabling the security module.
On R1
The security module must be enable on the router, by enter the show version
R1#show version
<... omitid ...>
Technology Package License Information for Module:’c2900′
—————————————————————-
Technology Technology-package Technology-package
Current Type Next reboot
—————————————————————–
ipbase ipbasek9 Permanent ipbasek9
security disable None None
uc disable None None
data disable None None
Configuration register is 0x2102
<... omitid...>
To enable the security module:
R1(config)#license boot module c2900 technology-package securityk9
<... omitid..>
Activation of the software command line interface will be evidence of
your acceptance of this agreement.
ACCEPT? [yes/no]: y
% use ‘write’ command to make license boot config take effect on next boot
%LICENSE-6-EULA_ACCEPTED: EULA for feature securityk9 1.0 has been accepted. UDI=CISCO2911/K9:FTX1524C8B3; StoreIndex=0:Evaluation License Storage
R1(config)#: %IOS_LICENSE_IMAGE_APPLICATION-6-LICENSE_LEVEL: Module name = C2900 Next reboot level = securityk9 and License = securityk9
Save the runing-config to start and reload the router
R1#copy run start
Destination filename [startup-config]?
Building configuration…
[OK]
R1#reload
Proceed with reload? [confirm]
After reload the router, issue again the show version command
R1#show version
<... omitid..>
Technology Package License Information for Module:’c2900′
—————————————————————-
Technology Technology-package Technology-package
Current Type Next reboot
—————————————————————–
ipbase ipbasek9 Permanent ipbasek9
security securityk9 Evaluation securityk9
uc disable None None
data disable None None
Configuration register is 0x2102
Note. The repeat the configuration on the router on other side, in that case on R3
R3(config)#license boot module c2900 technology-package securityk9
R3(config)#exit
R3#copy running-config startup-config
R3#reload
R3#show version
<... omitid..>
Technology Package License Information for Module:’c2900′
—————————————————————-
Technology Technology-package Technology-package
Current Type Next reboot
—————————————————————–
ipbase ipbasek9 Permanent ipbasek9
security securityk9 Evaluation securityk9
uc disable None None
data disable None None
Configuration register is 0x2102
e.3 Configuring IPsec paramters
R1(config)#access-list 101 permit gre 192.168.16.0 0.0.0.255 172.16.2.0 0.0.0.255
R1(config)#crypto ?
dynamic-map Specify a dynamic crypto map template
ipsec Configure IPSEC policy
isakmp Configure ISAKMP policy
key Long term key operations
map Enter a crypto map
R1(config)#crypto isakmp ?
client Set client configuration policy
enable Enable ISAKMP
key Set pre-shared key for remote peer
policy Set policy for an ISAKMP protection suite
R1(config)#crypto isakmp policy ?
><1-10000> Priority of protection suite
R1(config)#crypto isakmp policy 101
R1(config-isakmp)#encryption ?
3des Three key triple DES
aes AES – Advanced Encryption Standard
des DES – Data Encryption Standard (56 bit keys).
R1(config-isakmp)#encryption aes ?
128 128 bit keys.
192 192 bit keys.
256 256 bit keys.
R1(config-isakmp)#encryption aes
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group ?
1 Diffie-Hellman group 1
2 Diffie-Hellman group 2
5 Diffie-Hellman group 5
R1(config-isakmp)#group 5
R1(config-isakmp)#exit
R1(config)#crypto isakmp key cisco address 170.16.6.1
R1(config)#
Configure the ISAKMP phase 2 properties on R1 and R3
Create the transform-set VPN-SET to use esp-aes and esp-sha-hmac.
Then create the crypto map VPN-MAP that binds all of the Phase 2 parameters together.
Use sequence number 10 and identify it as
an ipsec-isakmp map
R1(config)#crypto ipsec ?
security-association Security association parameters
transform-set Define transform and settings
R1(config)#crypto ipsec transform-set ?
WORD Transform set tag
R1(config)#crypto ipsec transform-set R1_R3_SET ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
esp-3des ESP transform using 3DES(EDE) cipher (168 bits)
esp-aes ESP transform using AES cipher
esp-des ESP transform using DES cipher (56 bits)
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-sha-hmac ESP transform using HMAC-SHA auth
R1(config)#crypto ipsec transform-set R1_R3_SET esp-aes ?
128 128 bit keys.
192 192 bit keys.
256 256 bit keys.
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-sha-hmac ESP transform using HMAC-SHA auth
R1(config)#crypto ipsec transform-set R1_R3_SET esp-aes esp-sha-hmac
R1(config)#crypto map ?
WORD Crypto map tag
ipv6 IPv6 crypto map
R1(config)#crypto map R1_R3_Map ?
><1-65535> Sequence to insert into crypto map entry
client Specify client configuration settings
isakmp Specify isakmp configuration settings
R1(config)#crypto map R1_R3_Map 101 ?
ipsec-isakmp IPSEC w/ISAKMP
R1(config)#crypto map R1_R3_Map 101 ipsec-isakmp ?
dynamic Enable dynamic crypto map support
R1(config)#crypto map R1_R3_Map 101 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R1(config-crypto-map)#set peer ?
A.B.C.D IP address of peer
R1(config-crypto-map)#set peer 170.16.6.1
R1(config-crypto-map)#match ?
address Match address of packets to encrypt.
R1(config-crypto-map)#match address ?
<100-199> IP access-list number
WORD Access-list name
R1(config-crypto-map)#match address 101
Configure the crypto map on the outgoing interface
R1(config)#interface g0/1
R1(config-if)#crypto ?
map Assign a Crypto Map
R1(config-if)#crypto map ?
WORD Crypto Map tag
R1(config-if)#crypto map R1_R3_Map
*Jan 3 07:16:26.785: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Repeat the same configuration on R3 changing the appropriate IP address.
R3(config)#crypto isakmp key cisco address 172.16.2.2
R3(config)#crypto ipsec transform-set R3_R1_SET esp-aes esp-sha-hmac
R3(config)#!
R3(config)#crypto map R3_R1_Map 101 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R3(config-crypto-map)# set peer 172.16.2.2
R3(config-crypto-map)# match address 101
R3(config)#interface serial0/3/1
R3(config-if)#crypto ?
map Assign a Crypto Map
R3(config-if)#crypto map ?
WORD Crypto Map tag
R3(config-if)#crypto map R3_R1_Map?
WORD
R3(config-if)#crypto map R3_R1_Map ?
R3(config-if)#crypto map R3_R1_Map
*Jan 3 07:16:26.785: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Verify connectivity
Attempt to ping R3(170.16.6.1) from R1
R1#ping 170.16.6.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 170.16.6.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/5 ms
Attempt to ping R1(172.16.2.2) from R3
R3#ping 172.16.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/21/105 ms
Download now the PKT file of “Configuring CCNA&RS VTP HSTP GRE IPsec EIGRP Done Cisco Packet Tracer 7.0″
[download id=”4338”]
Lab, simulation, configuring PPPoE client&server side GNS3
Lab, simulation, configuring PPPoE client&server side GNS3
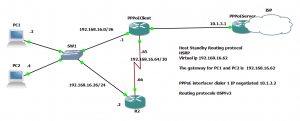
Step 1 Configuring PPPoE Server side
PPPoEServer#conf t
Enter configuration commands, one per line. End with CNTL/Z.
PPPoEServer(config)#bb?
bba-group
PPPoEServer(config)#bba-group ?
pppoe PPPoE type
PPPoEServer(config)#bba-group pppoe ?
WORD BBA Group name
global PPPoE global group
PPPoEServer(config)#bba-group pppoe UKgoodbyeGroup
PPPoEServer(config-bba-group)#
*Sep 6 11:41:03.807: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up
PPPoEServer(config-bba-group)#
*Sep 6 11:41:03.815: %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to up
PPPoEServer(config-bba-group)#virtual-template ?
Virtual Template interface number
PPPoEServer(config-bba-group)#virtual-template 26
PPPoEServer(config-bba-group)#?
BBA Group configuration commands:
control-packets PPPoE control packets related configuration
default Set a command to its defaults
exit Exit from BBA Group configuration mode
limit limit contents of pppoe control messages
mac-address Set mac address
nas-port Specific format for nas-port
nas-port-id Specific format for nas-port-id
no Negate a command or set its defaults
pado PADO delay options
pppoe PPPoE server selection configuration
service Services to be associated with this group
sessions BBA session commands
tag Configure processing options for a tag
vendor-tag PPPoE Vendor Specific Tag
virtual-template BBA virtual template command
PPPoEServer(config-bba-group)#sessions per-mac limit 2
PPPoEServer(config-bba-group)#exit
PPPoEServer(config)#interface virtual-template ?
Virtual-Template interface number
PPPoEServer(config)#interface virtual-template 26
PPPoEServer(config-if)#ip address 10.1.3.1 255.255.255.0
Authentication:
PPPoEServer(config-if)#ppp authentication chap callin
PPPoEServer(config-if)#peer default ip address ?
dhcp Use DHCP proxy client mechanism to allocate a peer IP address
dhcp-pool Use local DHCP pools to allocate a peer IP address
pool Use IP pool mechanism to allocate a peer IP address
PPPoEServer(config-if)#peer default ip address pool EUPool
PPPoEServer(config)#ip local pool EUPool 10.1.3.2 10.1.3.254
You must to create a username and password on the client side too.
PPPoEServer(config)#username Brexit password fromEU
Associate the interface of the server side:
PPPoEServer(config)#interface g4/0
PPPoEServer(config-if)#no ip address
PPPoEServer(config-if)#pppoe enable group UKgoodbyeGroup
PPPoEServer(config-if)#no shutdow
PPPoEServer(config-if)#
Step 2 Configuring PPPoE client side
PPPoEClient(config)#interface dialer 1
PPPoEClient(config-if)#dialer pool 1
PPPoEClient(config-if)#encapsulation ppp
The authentication from to client side to pppoe server, will as username “Brexit” and password “fromEU”.
PPPoEClient(config-if)#ppp chap hostname Brexit
PPPoEClient(config-if)#ppp chap password fromEU
PPPoEClient(config-if)#ip address negotiated
The MTU is 1500-8= 1492, because the PPP header adds 8 bytes of overhead to each frame.
PPPoEClient(config-if)#mtu ?
MTU size in bytes
PPPoEClient(config-if)#mtu 1492
PPPoEClient(config-if)#exi
PPPoEClient(config)#interface g4/0
PPPoEClient(config-if)#no ip address
PPPoEClient(config-if)#pppoe-client ?
dial-pool-number dialer pool keyword
ppp-max-payload Send PPP Max-Payload tag in PPPoE control packets
PPPoEClient(config-if)#pppoe-client dial-pool-number ?
Dialer pool number
PPPoEClient(config-if)#pppoe-client dial-pool-number 1
PPPoEClient(config-if)#no shutdown
PPPoEClient(config-if)#
The PPPoE session has successfully formed
*Sep 6 12:28:59.347: %DIALER-6-BIND: Interface Vi1 bound to profile Di1
PPPoEClient(config-if)#
*Sep 6 12:28:59.359: %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to up
PPPoEClient(config-if)#
*Sep 6 12:29:00.039: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up
Step 3 Verification
PPPoEClient#show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 192.168.16.1 YES manual up up
Serial5/0 192.168.16.65 YES manual up up
Dialer1 10.1.3.2 YES IPCP up up
PPPoEClient#
The show pppoe session shows the session stablished on dialer 1 via GigabitEthernet4/0
PPoEClient#show pppoe session
1 client session
Uniq ID PPPoE RemMAC Port VT VA State
SID LocMAC VA-st Type
N/A 16 ca03.1540.0070 Gi4/0 Di1 Vi1 UP
ca01.0410.0070 UP
PPPoEClient#
Download the GNS3 file for the simulation WAN PPPoE and OSPF as routing protocol
[download id=”4137″]
Configuring PPP and CHAP
Configuring PPP and CHAP
The encapsulation is PPP and authentication is CHAP and the routing protocol configured is OSPFv2
Router R1
username R2 password 0 mychap
!
!
license udi pid CISCO2911/K9 sn FTX15245CQ7
!
!
spanning-tree mode pvst
!
!
interface GigabitEthernet0/0
ip address 172.16.1.1 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/2
no ip address
duplex auto
speed auto
shutdown
!
interface Serial0/3/0
ip address 172.16.2.1 255.255.255.252
encapsulation ppp
ppp authentication chap
!
interface Serial0/3/1
no ip address
clock rate 2000000
shutdown
!
interface Vlan1
no ip address
shutdown
!
router ospf 1
log-adjacency-changes
network 172.16.2.0 0.0.0.3 area 0
network 172.16.1.0 0.0.0.255 area 0
!
Configuration on R2
username R1 password 0 mychap
!
!
license udi pid CISCO2911/K9 sn FTX1524O0PQ
!
!
!
!
spanning-tree mode pvst
!
interface GigabitEthernet0/0
ip address 172.16.3.1 255.255.255.252
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/2
no ip address
duplex auto
speed auto
shutdown
!
interface Serial0/3/0
ip address 172.16.2.2 255.255.255.252
encapsulation ppp
ppp authentication chap pap
clock rate 2000000
!
interface Serial0/3/1
no ip address
clock rate 2000000
shutdown
!
interface Vlan1
no ip address
shutdown
!
router ospf 2
log-adjacency-changes
network 172.16.3.0 0.0.0.255 area 0
network 172.16.2.0 0.0.0.3 area 0
!
Download here, the lab [download id=”4118″]

