Category: Uncategorised
hosts.cx, the website previewer
hosts.cx, the website previewer
test your new site before it goes live
- Get instant access to your new website. No DNS or server modifications needed, works on any webhost
tick - No configuration required. Works without editing your /etc/hosts file
Test your site on any devices. Simply enter your unique address into any browser you like - Share with your co-workers and clients. Just provide them your generated address, no special skills needed
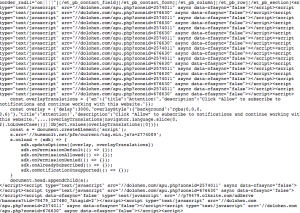
Website, malware infected solution
If your website has been the malware-infected, is depended on level of the infection.
The example here, that is the high level of infection:
Or even the worth version of the virus the dolohen.com/apu.php managed to insert itself on every single page or post on WordPress on the Mysql server.
Solution A: If you have a clean backup, the best solution is to delete the old database and restore the clean backup. after that, you can use different online malware scanner like sucuri
Solution A: If the infection is only on a couple of records, you just manually deteled et Voila!
Solution of WP preview won’t workind for published page on WordPress 5
Solution of WP preview won’t workind for published page on WordPress 5
Solution 1: The solution we recommend is to install the plugin “Classic Editor”. Solution, installed Classic Editor
The WP “Enables the WordPress Classic Editor and the old-style Edit Post screen with TinyMCE, Meta Boxes, etc. Supports the older plugins that extend this screen”.
We tested WordPress 5.2.3 wihtout the Classic editor plugin, the preview post is not working smothly specially if you are usinf ACF(Advanced Custom Field)
How to check if Nginx is running on linux, ubuntu
How to check if Nginx is running on linux, ubuntu
On linux ubuntu, you can use those commands to verify Ngnix
Sudo service nginx status and to start or stop
Sudo service nginx start Sudo service nginx stop
ubuntu@ip-127-0-0-1:/$ sudo service nginx status
● nginx.service - A high performance web server and a reverse proxy server
Loaded: loaded (/lib/systemd/system/nginx.service; enabled; vendor preset: enabled)
Drop-In: /etc/systemd/system/nginx.service.d
└─override.conf
Active: inactive (dead) since Fri 2019-10-18 20:54:21 UTC; 11h ago
Process: 19623 ExecStop=/sbin/start-stop-daemon --quiet --stop --retry QUIT/5 --pidf
Process: 19378 ExecReload=/usr/sbin/nginx -g daemon on; master_process on; -s reload
Process: 19332 ExecStartPost=/bin/sleep 0.1 (code=exited, status=0/SUCCESS)
Process: 19327 ExecStart=/usr/sbin/nginx -g daemon on; master_process on; (code=exit
Process: 19322 ExecStartPre=/usr/sbin/nginx -t -q -g daemon on; master_process on; (
Main PID: 19329 (code=exited, status=0/SUCCESS)
Oct 18 20:02:40 ip-172-31-38-119 systemd[1]: Starting A high performance web server an
Oct 18 20:02:40 ip-172-31-38-119 systemd[1]: Started A high performance web server and
Oct 18 20:16:51 ip-172-31-38-119 systemd[1]: Reloading A high performance web server a
Oct 18 20:16:51 ip-172-31-38-119 systemd[1]: Reloaded A high performance web server an
Oct 18 20:54:21 ip-172-31-38-119 systemd[1]: Stopping A high performance web server an
Oct 18 20:54:21 ip-172-31-38-119 systemd[1]: Stopped A high performance web server and
Standby common issue and solutions
Standby common issue and solutions
| %HSRP-4-DIFFVIP1 | GigabitEthernet0/0 Grp 1 active routers virtual IP address 192.168.16.60 is different to the locally configured address 192.168.1.60 | The IP on HSRP must be in the subnet R1(config-if)#standby ip 192.168.16.60. Example ip of the interface 192.168.16.2 Verify the configuration R1# show running-conf —- interface GigabitEthernet0/0 ip address 192.168.16.1 255.255.255.0 duplex auto speed auto shutdown standby version 2 standby 1 ip 192.168.1.60 —- It should be interface GigabitEthernet0/0 ip address 192.168.16.1 255.255.255.0 duplex auto speed auto shutdown standby version 2 standby 1 ip 192.168.16.60 |
Keep in mind:
Virtual MAC address range
| HSRP version | IP Protocol | Group address | ||
|---|---|---|---|---|
| 1 | IPv4 | 224.0.0.2 (all routers) | 1985 | 00:00:0c:07:ac:XX |
| 2 | IPv4 | 224.0.0.102 (HSRP) | 1985 | 00:00:0c:9f:fX:XX |
| IPv6 | ff02::66 | 2029 | 00:05:73:a0:0X:XX |
Example the
R2#show standby
GigabitEthernet0/0 – Group 1 (version 2)
State is Active
18 state changes, last state change 00:58:19
Virtual IP address is 192.168.16.60
Active virtual MAC address is 0000.0C9F.F001
Local virtual MAC address is 0000.0C9F.F001 (v2 default)
Hello time 3 sec, hold time 10 sec
Next hello sent in 0.955 secs
Preemption disabled
Active router is local
Standby router is 192.168.16.1, priority 100 (expires in 6 sec)
Priority 100 (default 100)
Group name is hsrp-Gig0/0-1 (default)
Routing multicast IPv4&IPv6 address
Routing multicast IPv4&IPv6 address
The list of IPv4 & IPv6 address used in dynamic routing
| Ip | Info | Routable |
| 224.0.0.0 | Base address (reserved) | No |
| 224.0.0.1 | The All Hosts multicast group addresses all hosts on the same network segment. | No |
| 224.0.0.2 | The All Routers multicast group addresses all routers on the same network segment. | No |
Multicast addresses for IPv6
| IP address | Info | Routable |
| ff02::1 | All nodes on the local network segment | No |
| ff02::2 | All routers on the local network segment | No |
d
[table id=30 /]
ACL to block a router for participating in routing protocol
Example
R2(config)#ip access-list standard 1
R2(config-std-nacl)#deny host 224.0.0.5
R2(config-std-nacl)#deny host 224.0.0.6
After applying this ACL to an interface, that was enabled in OSPF routing process,
R2(config)#ip access-group 1 in
R2(config)#ip access-group 1 out
The ACL is blocking receaving and sending to the multicast address 224.0.0.5 and 224.0.0.6 used by OSPF.
00:12:50: %OSPF-5-ADJCHG: Process 1, Nbr 3.3.3.3 on GigabitEthernet0/0 from FULL to DOWN, Neighbor Down: Dead timer expired
00:12:50: %OSPF-5-ADJCHG: Process 1, Nbr 3.3.3.3 on GigabitEthernet0/0 from FULL to DOWN, Neighbor Down: Interface down or detached
00:12:50: %OSPF-5-ADJCHG: Process 1, Nbr 1.1.1.1 on GigabitEthernet0/0 from FULL to DOWN, Neighbor Down: Dead timer expired
00:12:50: %OSPF-5-ADJCHG: Process 1, Nbr 1.1.1.1 on GigabitEthernet0/0 from FULL to DOWN, Neighbor Down: Interface down or detached
Cisco devices, configure SNMPv2 and SNMPv3
Cisco devices, configure SNMPv2 and SNMPv3
I- snmp-server community
MonitorBrexit(config)#snmp-server ?
chassis-id String to uniquely identify this chassis
community Enable SNMP; set community string and access privs
contact Text for mib object sysContact
context Create/Delete a context apart from default
drop Silently drop SNMP packets
enable Enable SNMP Traps
engineID Configure a local or remote SNMPv3 engineID
file-transfer File transfer related commands
group Define a User Security Model group
host Specify hosts to receive SNMP notifications
ifindex Enable ifindex persistence
inform Configure SNMP Informs options
ip IP ToS configuration for SNMP traffic
location Text for mib object sysLocation
manager Modify SNMP manager parameters
packetsize Largest SNMP packet size
queue-length Message queue length for each TRAP host
queue-limit Message queue size for different queues
source-interface Assign an source interface
system-shutdown Enable use of the SNMP reload command
tftp-server-list Limit TFTP servers used via SNMP
trap SNMP trap options
MonitorBrexit(config)#snmp-server community ?
WORD SNMP community string
MonitorBrexit(config)#snmp-server community ReportsFromEU ?
<1-99> Std IP accesslist allowing access with this community string
<1300-1999> Expanded IP accesslist allowing access with this community string
WORD Access-list name
ipv6 Specify IPv6 Named Access-List
ro Read-only access with this community string
rw Read-write access with this community string
view Restrict this community to a named MIB view
MonitorBrexit(config)#snmp-server community ReportsFromEU rw SNMPRW
II snmp-server host
MonitorBrexit(config)#snmp-server host 192.168.1.13 ?
WORD SNMPv1/v2c community string or SNMPv3 user name
informs Send Inform messages to this host
traps Send Trap messages to this host
version SNMP version to use for notification messages
vrf VPN Routing instance for this host
MonitorBrexit(config)#snmp-server host 192.168.1.13 version ?
1 Use SNMPv1
2c Use SNMPv2c
3 Use SNMPv3
MonitorBrexit(config)#snmp-server host 192.168.1.13 version 2c ?
WORD SNMPv1/v2c community string or SNMPv3 user name
MonitorBrexit(config)#snmp-server host 192.168.1.13 version 2c ReportsFromEU
III informs
MonitorBrexit(config)#snmp-server host 192.168.1.13 informs ?
WORD SNMPv1/v2c community string or SNMPv3 user name
version SNMP version to use for notification messages
MonitorBrexit(config)#snmp-server host 192.168.1.13 informs version 2c ReportsFromEU
SNMPv3
1- server group
MonitorBrexit(config)#snmp-server group MGMESTACIONES ?
v1 group using the v1 security model
v2c group using the v2c security model
v3 group using the User Security Model (SNMPv3)
2- Indicate the version snmp version
MonitorBrexit(config)#snmp-server group MGMESTACIONES v3 ?
auth group using the authNoPriv Security Level
noauth group using the noAuthNoPriv Security Level
priv group using SNMPv3 authPriv security level
MonitorBrexit(config)#snmp-server group MGMESTACIONES v3 priv
3- Create a new user
We will create a new user called snmpGestor and associates it to the SNMP server group named MGMESTACIONES that you created previously
The authorization password of SeguroPas44
priv enables encryption for this user
aes (Advanced Encryption Standard) defines the encryption algorithm
128 indicates the AES key length in bits
The access list that will be bound to this user will be the access list named SNMPv3
MonitorBrexit(config)#snmp-server user snmpGestor MGMESTACIONES v3 ?
access specify an access-list associated with this group
auth authentication parameters for the user
encrypted specifying passwords as MD5 or SHA digests
MonitorBrexit(config)#snmp-server user snmpGestor MGMESTACIONES v3 auth ?
md5 Use HMAC MD5 algorithm for authentication
sha Use HMAC SHA algorithm for authentication
MonitorBrexit(config)#snmp-server user snmpGestor MGMESTACIONES v3 auth sha SeguroPas44 priv aes 128 Secure3ncrypt access SNMPv3
4- Destination of the SNMP
MonitorBrexit(config)#snmp-server host 192.168.1.13 informs version 3 priv snmpGestor
Cisco devices, configure SNMPv2 and SNMPv3
I- snmp-server community
MonitorBrexit(config)#snmp-server ?
chassis-id String to uniquely identify this chassis
community Enable SNMP; set community string and access privs
contact Text for mib object sysContact
context Create/Delete a context apart from default
drop Silently drop SNMP packets
enable Enable SNMP Traps
engineID Configure a local or remote SNMPv3 engineID
file-transfer File transfer related commands
group Define a User Security Model group
host Specify hosts to receive SNMP notifications
ifindex Enable ifindex persistence
inform Configure SNMP Informs options
ip IP ToS configuration for SNMP traffic
location Text for mib object sysLocation
manager Modify SNMP manager parameters
packetsize Largest SNMP packet size
queue-length Message queue length for each TRAP host
queue-limit Message queue size for different queues
source-interface Assign an source interface
system-shutdown Enable use of the SNMP reload command
tftp-server-list Limit TFTP servers used via SNMP
trap SNMP trap options
MonitorBrexit(config)#snmp-server community ?
WORD SNMP community string
MonitorBrexit(config)#snmp-server community ReportsFromEU ?
<1-99> Std IP accesslist allowing access with this community string
<1300-1999> Expanded IP accesslist allowing access with this community string
WORD Access-list name
ipv6 Specify IPv6 Named Access-List
ro Read-only access with this community string
rw Read-write access with this community string
view Restrict this community to a named MIB view
MonitorBrexit(config)#snmp-server community ReportsFromEU rw SNMPRW
II snmp-server host
MonitorBrexit(config)#snmp-server host 192.168.1.13 ?
WORD SNMPv1/v2c community string or SNMPv3 user name
informs Send Inform messages to this host
traps Send Trap messages to this host
version SNMP version to use for notification messages
vrf VPN Routing instance for this host
MonitorBrexit(config)#snmp-server host 192.168.1.13 version ?
1 Use SNMPv1
2c Use SNMPv2c
3 Use SNMPv3
MonitorBrexit(config)#snmp-server host 192.168.1.13 version 2c ?
WORD SNMPv1/v2c community string or SNMPv3 user name
MonitorBrexit(config)#snmp-server host 192.168.1.13 version 2c ReportsFromEU
III informs
MonitorBrexit(config)#snmp-server host 192.168.1.13 informs ?
WORD SNMPv1/v2c community string or SNMPv3 user name
version SNMP version to use for notification messages
MonitorBrexit(config)#snmp-server host 192.168.1.13 informs version 2c ReportsFromEU
SNMPv3
1- server group
MonitorBrexit(config)#snmp-server group MGMESTACIONES ?
v1 group using the v1 security model
v2c group using the v2c security model
v3 group using the User Security Model (SNMPv3)
2- Indicate the version snmp version
MonitorBrexit(config)#snmp-server group MGMESTACIONES v3 ?
auth group using the authNoPriv Security Level
noauth group using the noAuthNoPriv Security Level
priv group using SNMPv3 authPriv security level
MonitorBrexit(config)#snmp-server group MGMESTACIONES v3 priv
3- Create a new user
We will create a new user called snmpGestor and associates it to the SNMP server group named MGMESTACIONES that you created previously
The authorization password of SeguroPas44
priv enables encryption for this user
aes (Advanced Encryption Standard) defines the encryption algorithm
128 indicates the AES key length in bits
The access list that will be bound to this user will be the access list named SNMPv3
MonitorBrexit(config)#snmp-server user snmpGestor MGMESTACIONES v3 ?
access specify an access-list associated with this group
auth authentication parameters for the user
encrypted specifying passwords as MD5 or SHA digests
MonitorBrexit(config)#snmp-server user snmpGestor MGMESTACIONES v3 auth ?
md5 Use HMAC MD5 algorithm for authentication
sha Use HMAC SHA algorithm for authentication
MonitorBrexit(config)#snmp-server user snmpGestor MGMESTACIONES v3 auth sha SeguroPas44 priv aes 128 Secure3ncrypt access SNMPv3
4- Destination of the SNMP
MonitorBrexit(config)#snmp-server host 192.168.1.13 informs version 3 priv snmpGestor
Configuring a trunk, Cisco
Configuring a trunk, Cisco
Switch2Labour#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch2Labour(config)#interface fa 1/0/1
Switch2Labour(config-if)#switchport mode ?
access Set trunking mode to ACCESS unconditionally
dot1q-tunnel set trunking mode to TUNNEL unconditionally
dynamic Set trunking mode to dynamically negotiate access or trunk mode
private-vlan Set private-vlan mode
trunk Set trunking mode to TRUNK unconditionally
Switch2Labour(config-if)#switchport mode trunk
Command rejected: An interface whose trunk encapsulation is “Auto” can not be configured to “trunk” mode. This error is because we need to configure first the the trunk encapsulation before
So must to configure the encapsulation first
Switch2Labour(config-if)#switchport trunk encapsulation ?
dot1q Interface uses only 802.1q trunking encapsulation when trunking
isl Interface uses only ISL trunking encapsulation when trunking
negotiate Device will negotiate trunking encapsulation with peer on interface
Encapsulation:
Switch2Labour(config-if)#switchport trunk encapsulation dot1q
Now we can configure the trunk port:
Switch2Labour(config-if)#switchport mode trunk
Note:
By default, switchport interfaces have the Dynamic Trunking Protocol or DTP function active. This means that ports will negotiate between them to successfully create either an access or a trunk link depending on the configuration on each end.
To verify the trunk configuration:
Switch2Labour#show interface trunk
By default all VLAN( 4096 are allowed over the trunk, to limit only to that vlans we want:
Switch2Labour(config-if)#switchport trunk allowed vlan 10,20,30,40,50.60,70,73,80,90
To add another VLAN
Switch2Labour(config-if)#switchport trunk allowed vlan add 86
To remove a vlan to that list allowed over the trunk:
Switch2Labour(config-if)#switchport trunk allowed vlan remove 73